|
PHP development can benefit greatly from the use of SSH and Public-key authentication. The role of Public and Private keys is explained in PHP Security scenario and now we just need to make the keys. How? There are two ways to do it:
- Follow the numerous instructions widely available on the web
- Or if your SSH server is openssh you may use the key generator built-in into PhpED
|
 |
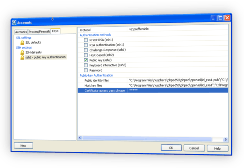 |
How to generate the Keys in PHP IDE
- Go to Tools->Accounts and select the Keys tab. Bring up the popup menu SSH settings -> New -> SSH settings, it will ask you if you want to create keys (certificates). Select "Yes" to generate the keys. Each SSH settings defines 3 things
- Version of the protocol
- Type of the authentication
- Generation of the set of keys
- PHP IDE generates 3 sets of public/private key pairs :
- RSA for v1 (identity.pub, identity),
- RSA for v2 (id_rsa.pub, id_rsa)
- DSA for v2 (id_dsa.pub, id_dsa)
- Protocol.
At this time almost all servers are using v2 version of SSH. PhpED provides 4 options in Protocol values dropdown list:
- "v1 preferrable" - if selected PHP IDE will try connecting using v1 and if the server doesn't support it switch to v2.
- "v2 perferrable" -same as above but trying v2 first and then v1.
- The other two options mean using v1 or v2 only.
- Authentication Methods
- RHost RSA (ssh1) - old host-based variation of ssh authentication supported only in v1.
- Host-based (ssh2) - old variation of ssh authentication supported only in v2 version of SSH protocol.
- Server side settings for RHost RSA (ssh1) and Host-based (ssh2): host-based authenticates by identifying the host and the user. Host identification is done by the server using a line in the file $HOME/.ssh/known_hosts. The user is identified using $HOME/.rhosts:
- $HOME/.rhosts should contain the line with the name (or address) of the client computer (host) and the name of the LOCAL user - i.e. the name used to identify the user to the local OS (Windows), separated by white space. Each unique address<->user pair must be entered ona separate line. Addresses and user names don't have to be unique. For example:
- 192.168.0.12 Steve
- 192.168.0.15 Ann
- The address in $HOME/.ssh/known_hosts should be the same as in .rhost followed after a white space by the line from the file containing public key. Resulting line will look similar to this , for example for
- ssh v1:
192.168.0.12 1023 37 750264830475338225968156896275267251052745346787329972124979760435859 somecomment
- ssh v2
192.168.0.12 ssh-rsa AAAAB3Nza/jLtZ2i7CdSJIkGlX5hBDSM6bzZqwvPCkh2lsEVlsEC1yc2EAAAmew== somecomment
- Client Side settings (PhpED):
- From the Authentication Methods select the checkbox corresponding to server side settings and add the file name containing the private key in "Host key files". If the private key is protected with passphrase add "Certificate access pass phrase". This file permissions should be set to 0600 (user read/write only)
Warning: file known_hosts is located in the hidden subdirectory .ssh and the permissions on this file should be set to 0700 (user read/write/execute only )
- RSA Authentication (ssh1) - public key variation of ssh authentication, supported in protocol v1 only.
- Public key (ssh2) - public key varation of ssh authentication supported only in protocol v2
Public Key authentication uses a pair of RSA keys (default is identity.pub, identity for v1 and id_rsa.pub, id_rsa or id_dsa.pub, id_dsa for v2).
- If you already have the Key pair (2 files) already generated by the administrator you need to make sure that the file names are the same and the only difference is the file extensions - private key file should not have an extension, while the public key file can have any extension, as long as it is not empty. Public file should be added to the Public identity files" list. Pleas note that you don't need to add the Private key file to any lists, it will be found by the name of the Public key, which is why the names must be the same except for the extension. If the Private key protected with the passphrase, the phrase needs to be added to "Certificate access passphrase".
- Next you need to login to the server and copy the line from your Public key into $HOME/.ssh/authorized _keys. Make sure that it is copied as one line without white spaces and/or empty lines. Warning: the file authorized_keys is located in hidden directory .ssh and this file permissions should be set to 0700 (urer read/write/execute only). Permissions on the file authorized_keys must be 0600 (user read/write only)
- Pageant/RSA Authentication (ssh1) - this variation of public key ssh authentication is supported in v1 only.
- Pageant/Public key (ssh2) - this variation of ssh authentication is supported only in v2.
- Pageant Authentication works the same way as RSA Authentication (ssh1) and Public key (ssh2) with the only difference that the keys are fetched not from files but from the program peagant http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
If the Private key is protected by the passphrase the passphrase is entered when the key is entered in pageant. Fields "Public identity files", "Host key files" and "Certificate access passphrase" are not used.
- Server side settings should be the same as in RSA Authentication (ssh1)/Public key (ssh2).
- Challenge-Response (ssh1)
- Keyboard-Interactive (ssh2) Password
- As far as the user is concerned this is a regular password authentication. The only difference is that the password or some identification of the password is passed over protected channel, such that it can be checked on the server. You should check with your System Administrator which protocol is available on your system.
- Once you created SSH settings under some name, you can switch to the Accounts tab, select your sftp or ssh terminal account and select this name from the drop down in "SSH Setting" field.
- Supported key formats
- Version SSHv1 supports private keys in OpenSSH format. The file should have SSH PRIVATE KEY FILE FORMAT 1.1 in the beginning
Public key is stored in decimal formay as one string and looks like this
1023 37 750264830475338225968156896275267251052745346787329972124979760435859 somecomment
- Version SSHv2 supports private keys in PEM format (http://www.openssl.org/docs/apps/rsa.html) and starts with the line
-----BEGIN RSA PRIVATE KEY----- or -----BEGIN DSA PRIVATE KEY----- for rsa and dsa keys respectively. Public key is stored in base64 formatand looks like this:
ssh-rsa AAAAB3Nza/jLtZ2i7CdSJIkGlX5hBDSM6bzZqwvPCkh2lsEVlsEC1yc2EAAAmew== somecomment
- In any case the keys can be generated using openssh utility ssh-keygen, or exporting from putty into the format compatible with openssh. If your keys are protected with passphrase, don't forget to enter it into the "Certificate pass phrase" input
|
How to deploy the public Keys
|
Key deployment is described in the paragraph above, in addition to copying public key on to your server, please check with your server manual on where and how the key is recognized by server. In case of openssh server it is ~/.ssh/known_hosts file where ssh2-compatible key should be copy-pasted
|
Download the FREE trial of NuSphere's PhpED today!
|